Reaver is a tool to exploit the BruteForce vulnerability in WPS (WiFi Protected Setup). The guys at Tactical Network Solutions have written this tool Reaver. It is available in two versions, open source and commercial. Here's the Google Code link for Reaver :- http://code.google.com/p/reaver-wps/
We'll go through step-by-step to install Reaver 1.3 on BackTrack 5. This is a general step-by-step to install Reaver 1.3 on any Linux such as Ubutntu 11.09.
Installing Reaver is a simple process. We can directly download Reaver 1.3 using the wget command in the directory of our choice and then running the commands configure, make and make install. This should do it.
Step 1 :- Download Reaver 1.3
# wget http://reaver-wps.googlecode.com/files/reaver-1.3.tar.gz
Step 2 :- Extract Reaver 1.3
# tar zxvf reaver-1.3.tar.gz


Step 3 :- Browse to the directory where Reaver 1.3 is extracted.
# cd reaver-1.3/src

Step 4 :- Configure Command
# ./configure

Step 5 :- Make Command
# make

Step 6 :- Make Install Command
# make install
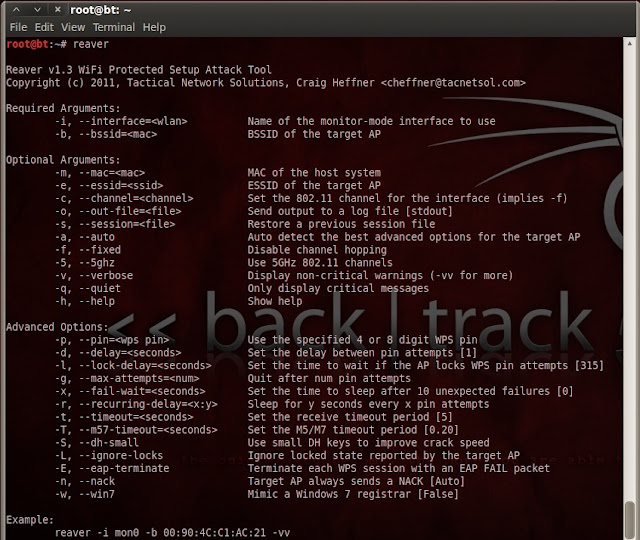
Step 7 :- Command to run Reaver
# reaver
Step 7 :- Command to run Walsh
# walsh
Walsh is the new utility that comes with Reaver. Using Walsh you can directly run the WPS BruteForce Attack on any AP in your vicinity.
Do leave comments, if you found this post helpful or not. :)
We'll go through step-by-step to install Reaver 1.3 on BackTrack 5. This is a general step-by-step to install Reaver 1.3 on any Linux such as Ubutntu 11.09.
Installing Reaver is a simple process. We can directly download Reaver 1.3 using the wget command in the directory of our choice and then running the commands configure, make and make install. This should do it.
Step 1 :- Download Reaver 1.3
# wget http://reaver-wps.googlecode.com/files/reaver-1.3.tar.gz
Step 2 :- Extract Reaver 1.3
# tar zxvf reaver-1.3.tar.gz
Step 3 :- Browse to the directory where Reaver 1.3 is extracted.
# cd reaver-1.3/src
Step 4 :- Configure Command
# ./configure
Step 5 :- Make Command
# make
Step 6 :- Make Install Command
# make install
Step 7 :- Command to run Reaver
# reaver

Step 7 :- Command to run Walsh
# walsh
Walsh is the new utility that comes with Reaver. Using Walsh you can directly run the WPS BruteForce Attack on any AP in your vicinity.
Do leave comments, if you found this post helpful or not. :)



In the screenshot above, is "mon0" an example of the ap or the name of the wifi adapter?
ReplyDeleteI assume you still need a non-usb wifi adapter that is capable of monitor-mode?
Ben, mon0 is the name of the wifi adapter. Walsh tool will automatically scan for the APs in range, so AP name need not be given as input.
ReplyDeleteWhen you put your wifi on monitor mode using airmon-ng, it creates a virtual wifi adapter called mon0.
Any wifi adapter, usb or non-usb should be capable of monitor-mode for this to work. Usually most of them support it.
# cd reaver-1.3/src
ReplyDeletede este paso no paso ya.. me pone que directorio no encontrado
Reaver 1.4 stuck at 99.99%
ReplyDeleteany solution sir? many thanks
I'm on Linux kali 4.9.0-kali3-amd64 #1 SMP Debian 4.9.13-1kali2 (2017-03-07) x86_64 GNU/Linux
ReplyDeleteI had to install apt-get install libpcap-dev sqlite3 libsqlite3-dev, because it needed the pcap and sql in order get it running.
No walsh btw in 1.4
This is not as helpful as I hoped. I know next to nothing about computer language and was not able to get through this guide on my windows 8/10 computer
ReplyDelete