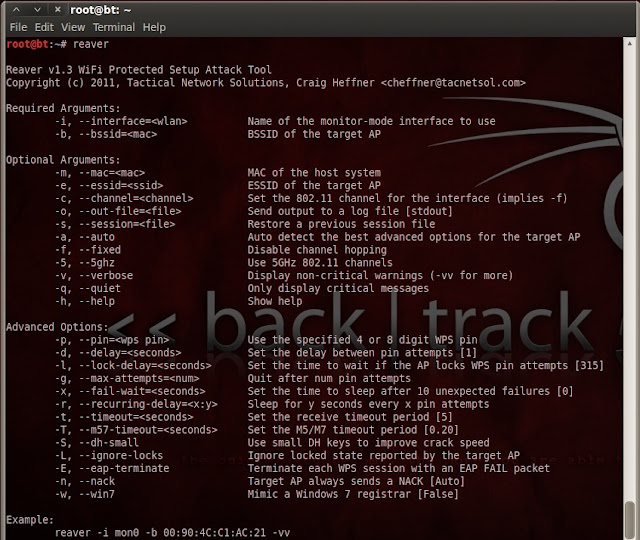
Reaver is the tool to exploit WPS bruteforce vulnerability.
Reaver is being updated really fast by Tactical Network Solutions. Reaver 1.4 is out now.
Following are step-by-step instructions on how to install Reaver 1.4 on BackTrack 5. If you already have Reaver 1.3 (or any other lower version) installed, then the following commands will uninstall it and update to Reaver 1.4.
You can find the Reaver source code on Google Code. Click here to download Reaver from Google Code.
Step 1 :- Download Reaver 1.4
# wget http://reaver-wps.googlecode.com/files/reaver-1.4.tar.gz
Step 2 :- Extract Reaver 1.4
# tar zxvf reaver-1.4.tar.gz
Step 3 :- Browse to the directory where Reaver 1.4 is extracted.
# cd reaver-1.4/src
Step 4 :- Configure Command
# ./configure
Step 5 :- Make Command
# make
Step 6 :- Make Install Command
# make install
Step 7 :- Command to run Reaver
# reaver
Step 7 :- Command to run Wash
# wash
Wash (previously called Walsh) is the utility that comes with Reaver 1.4. Wash automatically scans the APs in the range for the WPS bruteforce vulnerability.
Reaver is being updated really fast by Tactical Network Solutions. Reaver 1.4 is out now.
Following are step-by-step instructions on how to install Reaver 1.4 on BackTrack 5. If you already have Reaver 1.3 (or any other lower version) installed, then the following commands will uninstall it and update to Reaver 1.4.
You can find the Reaver source code on Google Code. Click here to download Reaver from Google Code.
Step 1 :- Download Reaver 1.4
# wget http://reaver-wps.googlecode.com/files/reaver-1.4.tar.gz
Step 2 :- Extract Reaver 1.4
# tar zxvf reaver-1.4.tar.gz
Step 3 :- Browse to the directory where Reaver 1.4 is extracted.
# cd reaver-1.4/src
Step 4 :- Configure Command
# ./configure
Step 5 :- Make Command
# make
Step 6 :- Make Install Command
# make install
Step 7 :- Command to run Reaver
# reaver
Step 7 :- Command to run Wash
# wash
Wash (previously called Walsh) is the utility that comes with Reaver 1.4. Wash automatically scans the APs in the range for the WPS bruteforce vulnerability.